As a follow-up to last Friday’s post about reviewing your cybersecurity plans, I have a real-world example for item #5 from that list: “Keep a very close eye on your websites and email clients to make sure they are not compromised and being used to spread malware or misinformation.”
Since the invasion of Ukraine, there’s been a huge uptick in spam misinformation from malicious Russian sources submitting comments that use compromised computers from countries outside of Russia.
This tactic is used to circumvent country wide blocks you can put in place for all web traffic originating from Russia. Hackers circumvent the process by using computers compromised from EU, UK, or North American locations. In these instances, hackers use a compromised computer to submit spam messages. In these instances, they are less concerned about gaining access to information. The only thing of value is the ability to hide the source of misinformation.
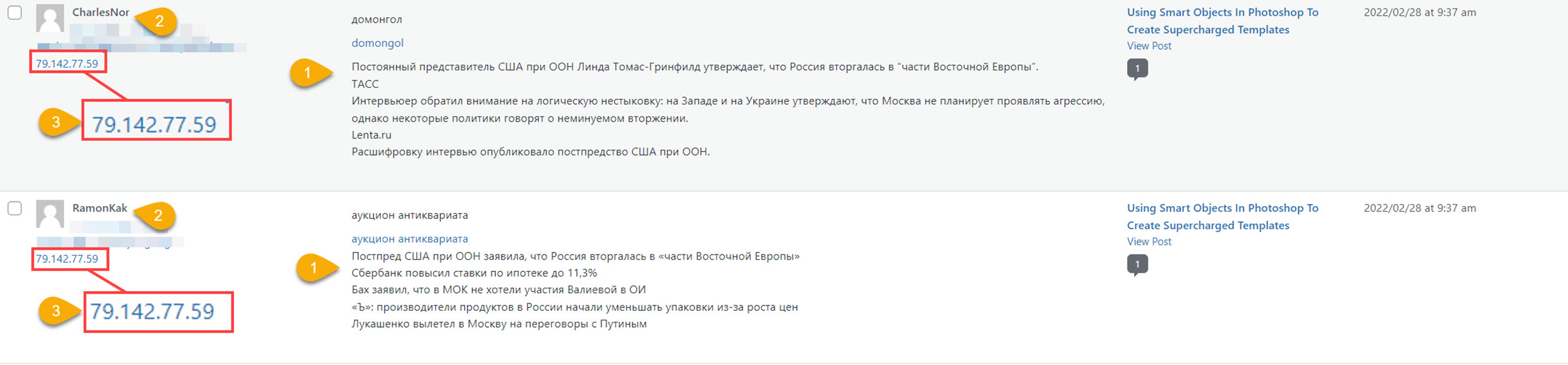
Here’s an example of two misinformation campaign messages that arrived Monday morning:
- The messages contain unique content. In this example, both are spreading misleading and false information. Repeating it here only serves their purpose, so I won’t bother.
- In an attempt to make the comments seem more legit, the username, email and website are unique between messages.
- This is the bit demonstrating that hackers are using compromised computers: this IP Address is in Stockholm, Sweden.
While most of this misinformation spam won’t see the light of day, that doesn’t matter to bad actors; for them, it’s all about quantity. It’s as simple as “throw enough mud against the wall…”
Don’t contribute to this unwittingly.
No doubt, it’s a pain in the ass to update passwords but doing so at your email clients, email marketing platforms, domain registrars, and websites will help cut down on this sort of malicious activity.